AVD: How to enable RDP Shortpath for Public Networks?

Since you are on this page, I’m assuming that you have or your clients have AVD implemented and are looking for ways to improve your environment. One of my favorite features is RDP Shortpath for Public Networks. Why? Clients and hosts are usually connected using something called “reverse connect”, which sends TCP outbound traffic through AVD gateway (using TCP 443) to the client machine. Due to this, there can be high latency, which can, for example, delay watching videos.
RDP Shortpath is a feature of Azure Virtual Desktop that establishes a direct UDP-based transport between Remote Desktop Client and Session host. RDP uses this transport to deliver Remote Desktop and RemoteApp while offering better reliability and consistent latency. For a complete overview please check the Microsoft doc.
Take a look at the diagram of RDP Shorpath Network Connection.

Let’s see how it looks from the client’s perspective.

Picture is captured from Microsoft blog post.
What steps should I take to implement this?
First of all, I would like to note that RDP Shortpath for Public Networks is still in preview, but I think it works great. I have not encountered any problems either in my testing environment or at clients’ sites.
Implementation is very simple.
To enable RDP Shortpath for Public Networks, follow these steps:
- Connect to the session host
- Open the elevated command prompt
- Enable the RDP Shortpath for public networks.
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations" /v ICEControl /t REG_DWORD /d 2 /fTo disable RDP Shortpath for Public Networks, follow these steps:
Follow the steps below to configure session host:
- Connect to the session host
- Open elevated command prompt
- Disable the RDP Shortpath for public networks.
REG DELETE "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations" /v ICEControl /fHow can I tell if RDP Shortpath is enabled?
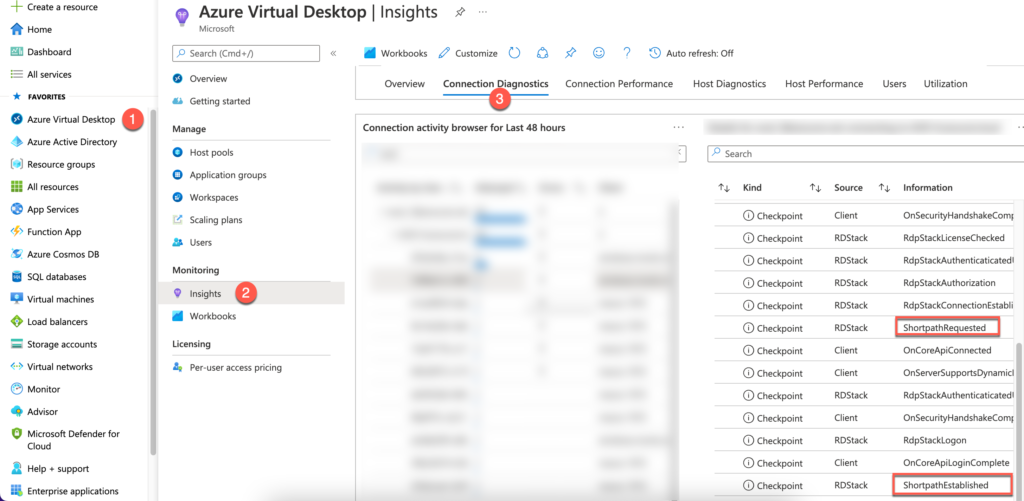
You can check if RDP Shortpath is working in many ways. If you want to verify that each client is using, you should look at Insights (Log Analytics).
From Azure Portal using Azure Virtual Desktop Insights
- Go to portal.azure.com > Azure Virtual Desktop > Insights > Connection Diagnostics > scroll all the way down to “Connection activity browser for Last 48 hours” – select the user and on the right side you can see information about ShortpathRequested and Established. See below.
From Azure Portal running a Query from Log Analytics
- Go to portal.azure.com > open Log Analytics Workspaces > select your workspace > under General click on Logs and run a Query.
WVDCheckpoints
| where Name contains "Shortpath"
What is the best way to check if RDP Shortpath is working from the clients’ machine?
This is probably the most common way to find out if RDP Shortpath is enabled.
- Once you establish connection from the client side (your/clients computer), check connection information. See below.

Once you open Connection information, show details.


RDP Shortpath does not work after I’ve done all of this. It still shows TCP. How can I fix this?
- Try rebooting your Session Host.
- Define your host pool as a validation host pool.
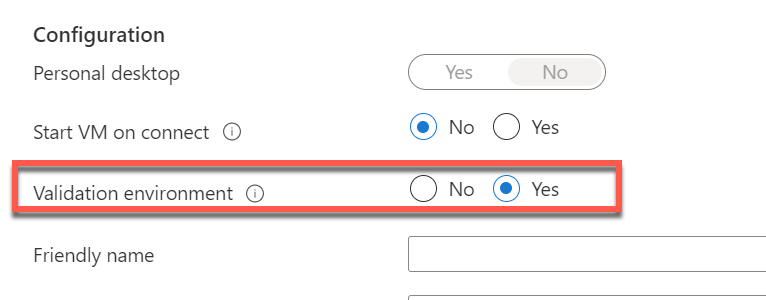
How to set Validation environment to Yes?
- Sign in to the Azure portal at https://portal.azure.com.
- Search for and select Azure Virtual Desktop.
- In the Azure Virtual Desktop page, select Host pools.
- Select the name of the host pool you want to edit.
- Select Properties.
- In the validation environment field, select Yes to enable the validation environment.
- Select Save to apply the new settings.
Does this work on Mac clients?
When connecting from Macs, it does not work. I tested this, and it always routed through TCP for some reason. I could not find any word about this on the Microsoft docs page.

That’s all there is to it. If you have any questions or issues, please let me know. I’m always here to help.
Hi. I also couldn’t get the macOS client to work via rdp shortpath, although it is indicated here that this function is supported from version 10.9.0 https://learn.microsoft.com/en-us/azure/virtual-desktop/whats-new -client-macos